How To import users and groups from AD/LDAP (advanced configuration)#
Importing users and groups from Active Directory into i-doit always takes place via the i-doit console utility command. For this we use the ldap-sync command.
At the end of the article there is a complete example of the created advanced configuration.
The article about configuration of LDAP directory/Active Directory should be known to everyone before.
Here we will go through different LDAP filters and a complete ldap.ini configuration.
The goal is to synchronize all users and groups from AD/LDAP with i-doit, as well as their memberships.
I assume a basic knowledge of AD/LDAP.
In these examples for persons the objectClass = user is used.
For groups the objectClass = group is used.
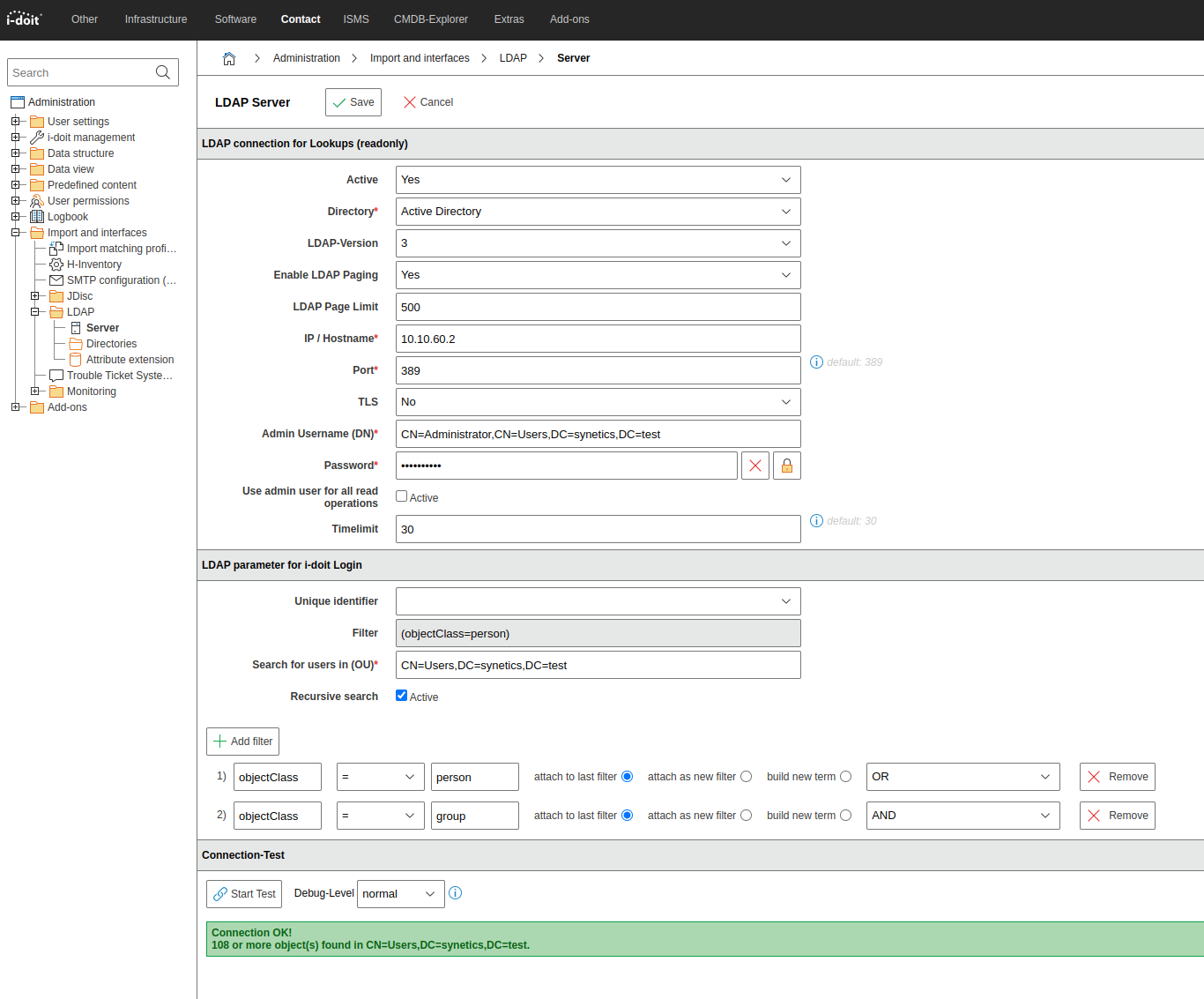
If you do not want to synchronize all users or groups of the domain, you have to enter the DN/CN of an OU or container under Search for users in (OU) *.
Filter configuration#
Import from all users#
Here only users are synchronized, which also means that no groups are created. So that only users are synchronized the filter must look like this:
1 | |
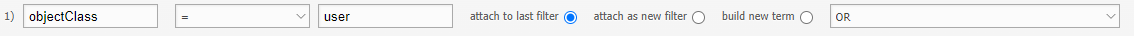
Import of users with specific attributes#
We want to filter on an attribute and synchronize only this user.
Only the user who has the value MichaelO in the attribute sAMAccountName should be synchronized.
1 | |
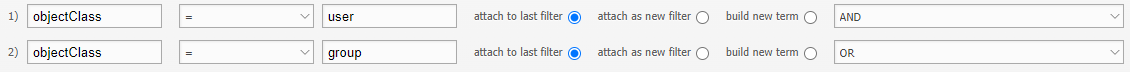
Import from all users and all groups#
Here users and groups are created and the users are assigned to the respective groups.
So that users and groups are synchronized the filter must look like this:
1 | |
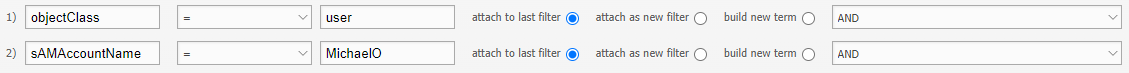
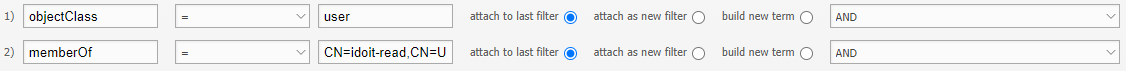
Import of users who are members of the idoit-read group#
To synchronize only users who are members of the idoit-read group, the filter must look like this:
1 | |
Import of users who are members of the group idoit-read and idoit-write#
To synchronize only users who are members of the idoit-read group, the filter must look like this:
1 | |
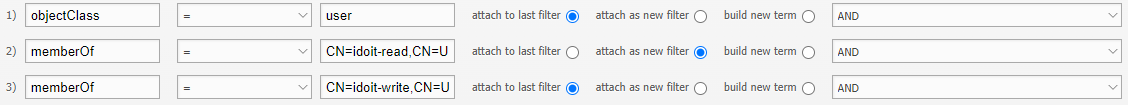
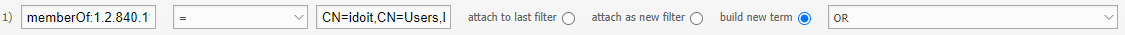
Import of users and groups that are below a nested group#
I have a group idoit in which the i-doit groups idoit-read and idoit-write are members. I want to synchronize these two groups. With this filter I can directly create the groups and the users.
This will not create the idoit group, it will only create the groups below it. Also, the groups will not be linked, because groups cannot have a group as a member.
1 | |
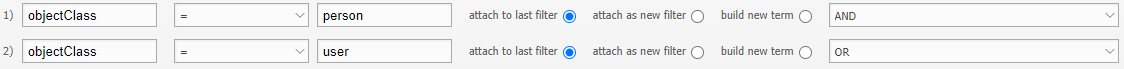
How to filter users with more than one objectClass#
For example, if the users differ by having two objectClass attributes (e.g. person and user), I would build the filter this way:
1 | |
Which other attributes can be imported via ldap.ini#
- The post ldap.ini Configuration should be known.
- An .ini file can be created for the import, with this additional attributes can be imported.
- The Category Extension should already be configured.
- We use the .ini section
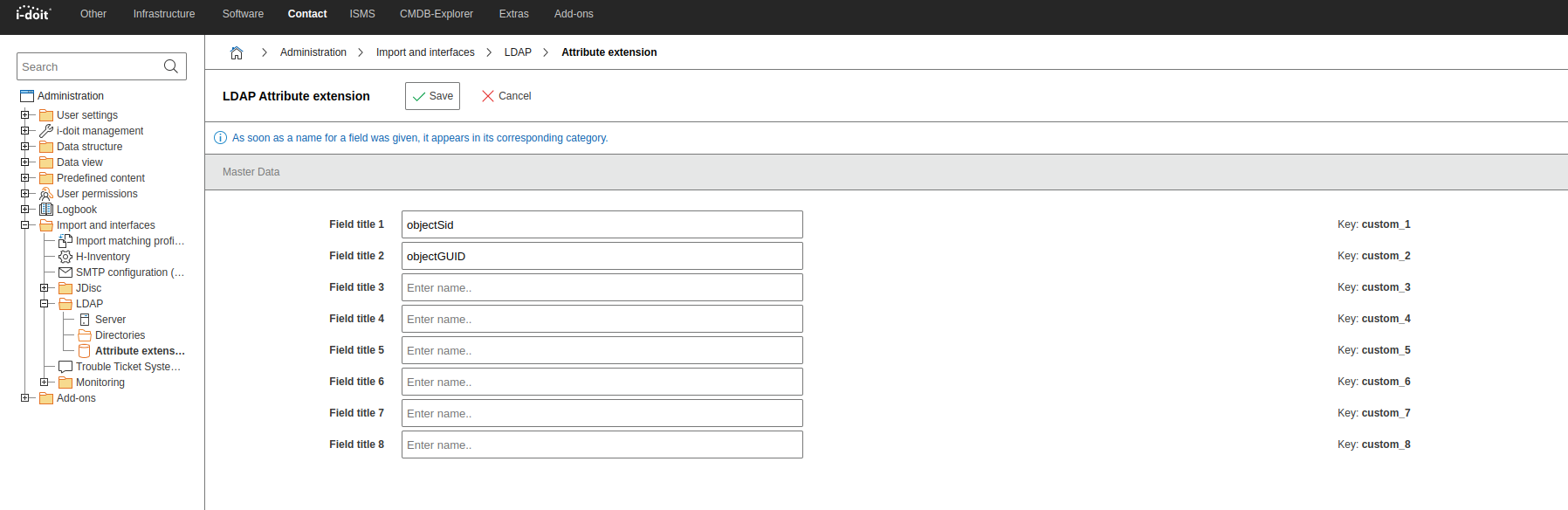
The configuration of the category extension#
Here again as a table
| Field title | Attribut | Mapping with |
|---|---|---|
| Field title 1 | objectSid | Key: custom_1 |
| Field title 2 | objectGUID | Key: custom_2 |
| Field title 3 | - | Key: custom_3 |
| Field title 4 | - | Key: custom_4 |
| Field title 5 | - | Key: custom_5 |
| Field title 6 | - | Key: custom_6 |
| Field title 7 | - | Key: custom_7 |
| Field title 8 | - | Key: custom_8 |
Attach users to Rooms statically#
Fixed assignments of users to rooms can be entered in the ldap.ini.
The users are then assigned to the assigned room as a contact.
(The rooms must exist in i-doit before!).
1 2 | |
Assign user as contact to rooms#
It is possible to assign persons as contact to rooms via the import_rooms function. Therefore you need to set the option to true. Rooms are created automatically, but without a location.
1 2 3 | |
Bug
Actually you will need to write this AD Attribute in lowercase physicaldeliveryofficename
How to import attributes from LDAP#
I want to import more LDAP attributes to users and I have already configured the category extension.
Now I have to configure the LDAP sync configuration file (ldap.ini).
Available attributes can be found in your AD configuration. From this I can search for the attributes that I want to synchronize additionally.
Which attributes belong to which field can be found via Google.
As an example I take the following attributes and add them to ldap.ini:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 | |
As you can see here I mapped the master data attribute department with the LDAP attribute department.
Additionally I used the category extension.
The structure for e.g.
1 | |
would be as follows, attributes tells the handler to synchronize the i-doit attribute [custom_1] with the LDAP attribute objectSid.
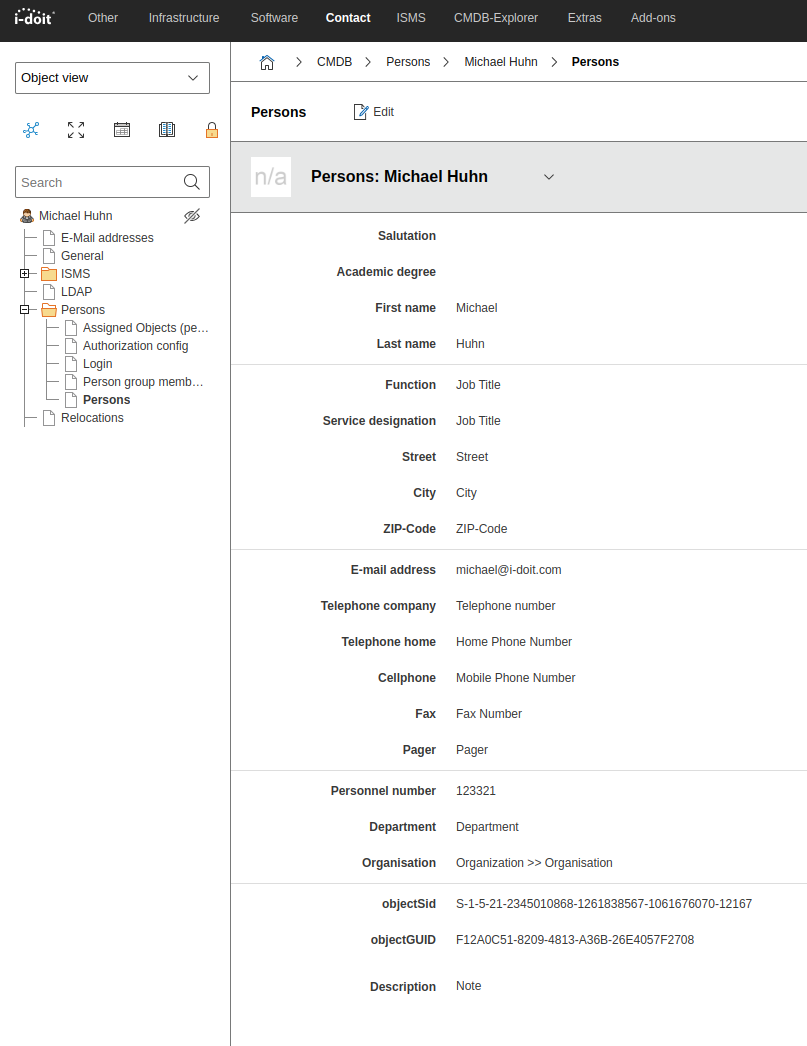
After synchronizing the users I find the following master data:
More options#
autoReactivateUsers#
This option will set all synchronized persons to Status = Normal. It will overwrite any other settings like, deletedUsersBehaviour or disabledUsersBehaviour.
This is helpful in case users were accidentally archived or deleted before.
Info
We should be aware that with NDS or OpenLDAP it is currently not possible to identify deleted users to archive them later. Users are then always activated! Manually performed changes will be overwritten.
1 | |
ignoreUsersWithAttributes#
Disable synchronization for users with attributes checked against ignoreFunction.
This function helps to prevent synchronization of unwanted directory objects.
The user will not be synchronized if ignoreFunction fails for ALL selected attributes.
By default it says ignoreUsersWithAttributes=[] so nothing will be ignored.
We only want to import users where the attributes samaccountname, sn, givenname and mail are not empty.
So the configuration for ignoreUsersWithAttributes should look like this:
1 2 3 4 | |
ignoreFunction#
Is the check function to ignore users (see ignoreUsersWithAttributes)
This can be any function name callable via call_user_func or the defined functions.
1 2 3 4 5 | |
Example: empty would be executed as empty($value)
We check for empty attributes with
1 | |
Synchronize empty attributes#
This option decides whether empty or emptied attributes from AD should be synchronized with i-doit or not.
1 | |
The complete ldap.ini#
Here is a finished ini. file which can of course be edited. The first part of the ldap.ini is obtained from Using Configuration Files for Console Commands.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 | |
On the console the command would look like this:
1 | |