Google authentifizierung via OpenID#
Requirements#
- Debian 10
- installed i-doit
- Server needs internet accessy
- Server needs a valid DNS name
- Server has to be reachable via SSL
- Access to Google APIs & Dienste
Create OAuth login credentials#
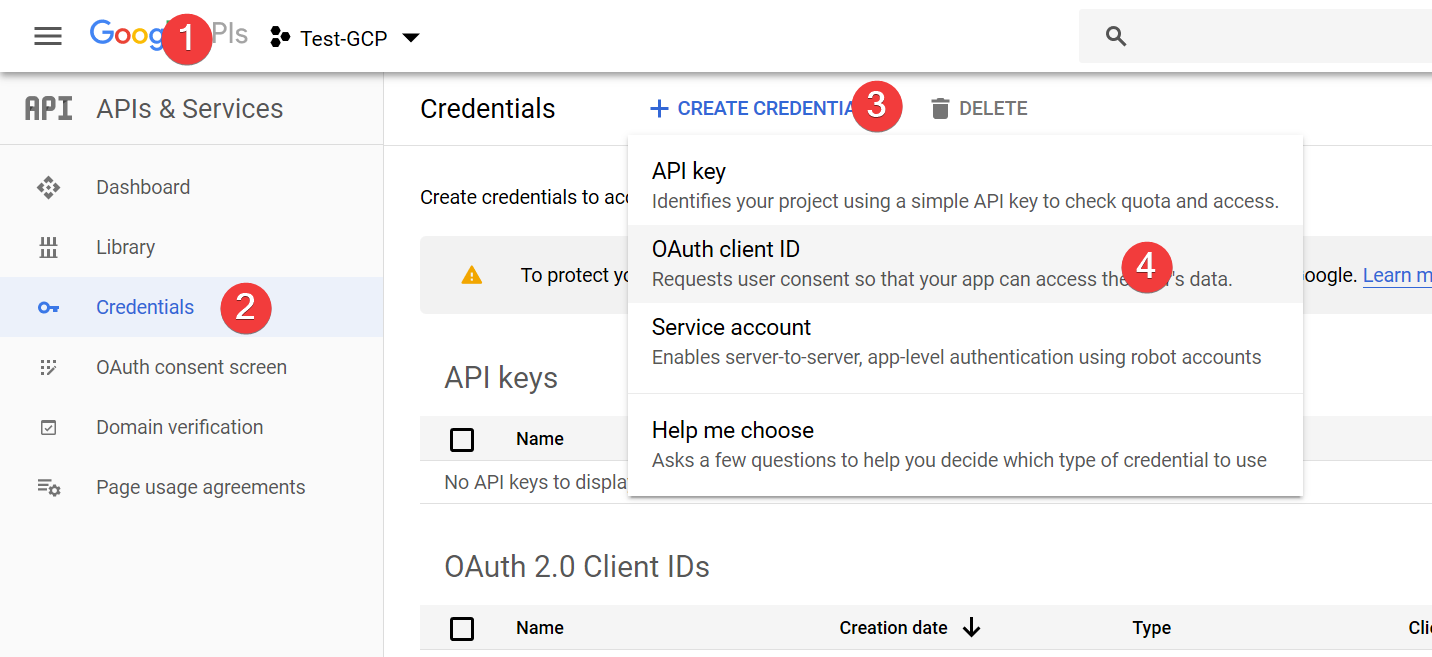
Open https://console.developers.google.com/
- Go the the home screen
- Select "Credentials"
- Select "Create Credentials"
- Select "OAuth client ID"
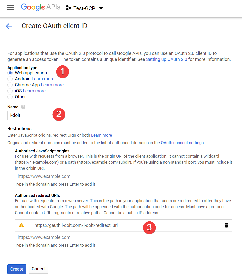
- Select "Web application"
- Use a recognizable title for the name
- Specify as Authorized Redirection URL a URL that is behind the web resource to be backed up but does not point to any content (!). The URL specified here as an example should be secured with authentication from https://gauth.i-doit.com/i-doit/. The attached resource "redirect_uri" does not exist on the web server!
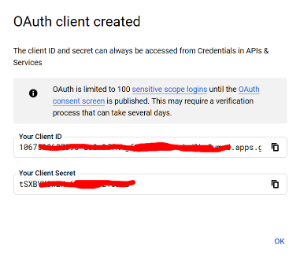
- Copy Client ID (will be needed later)
- Copy Client Secret (will be needed later)
- Configure OAuth approval screen (This is not neccessary for a test but will be needed on live systems)
Configure webserver#
Install the Apache package mod_auth_openidc in your installation of Debian 10#
1 | |
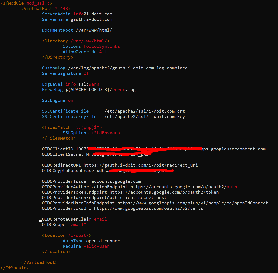
Add the following code to your Apache configuration:#
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 | |
This is how the configuration looks:#
Restart your webserver#
1 | |
Test authentication and finish last steps#
Create the file identity.php. In our case it will be created at /var/www/html/identity.php.
1 2 3 4 | |
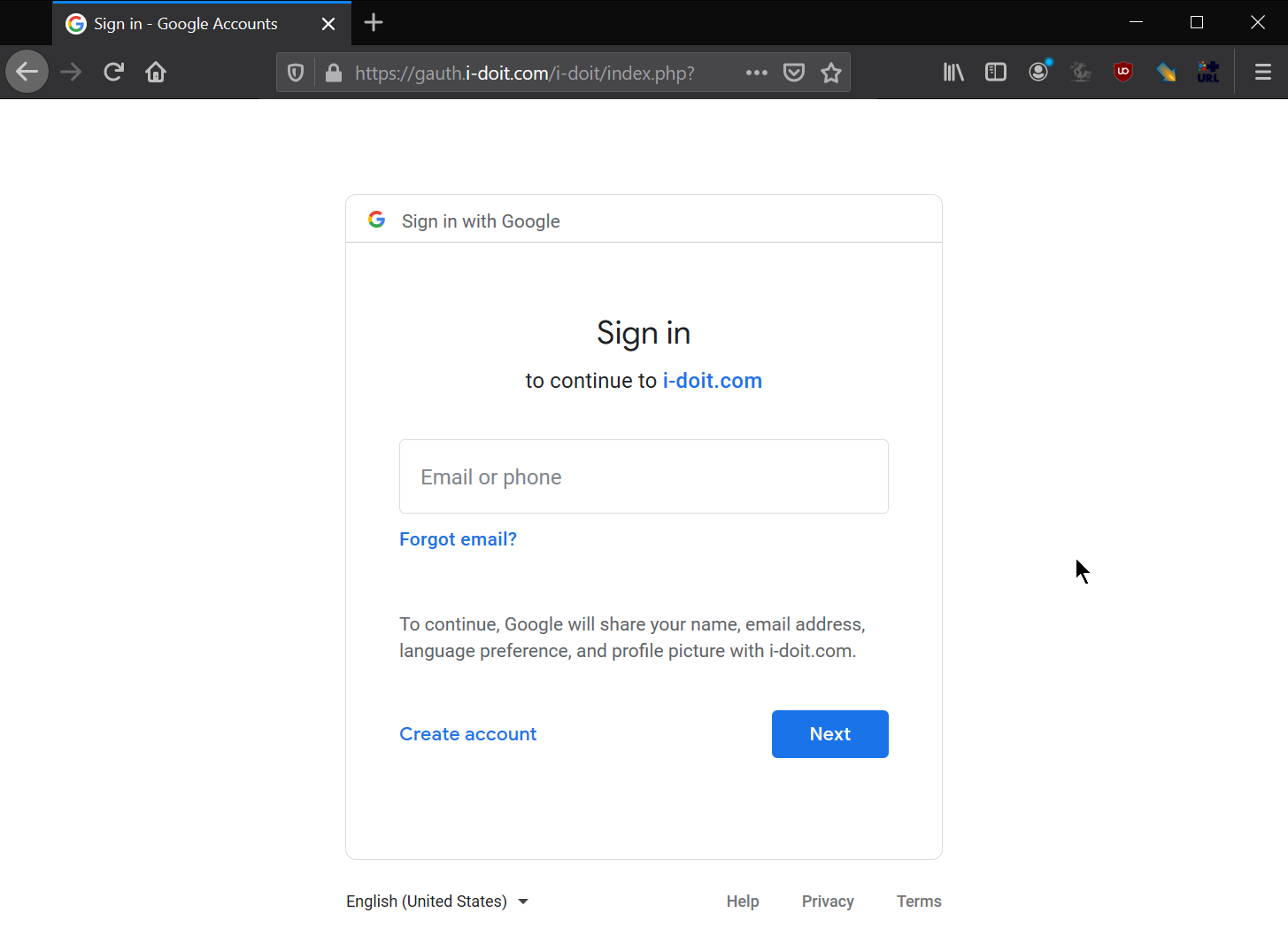
- Open the file in your browser
- Login via Google
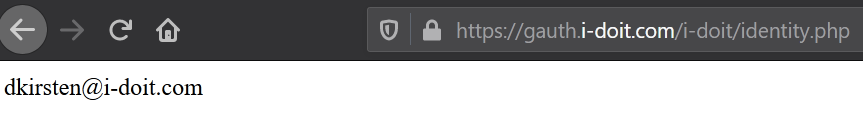
- Verify the displayed ID (This should be the ID from the e-mail address)
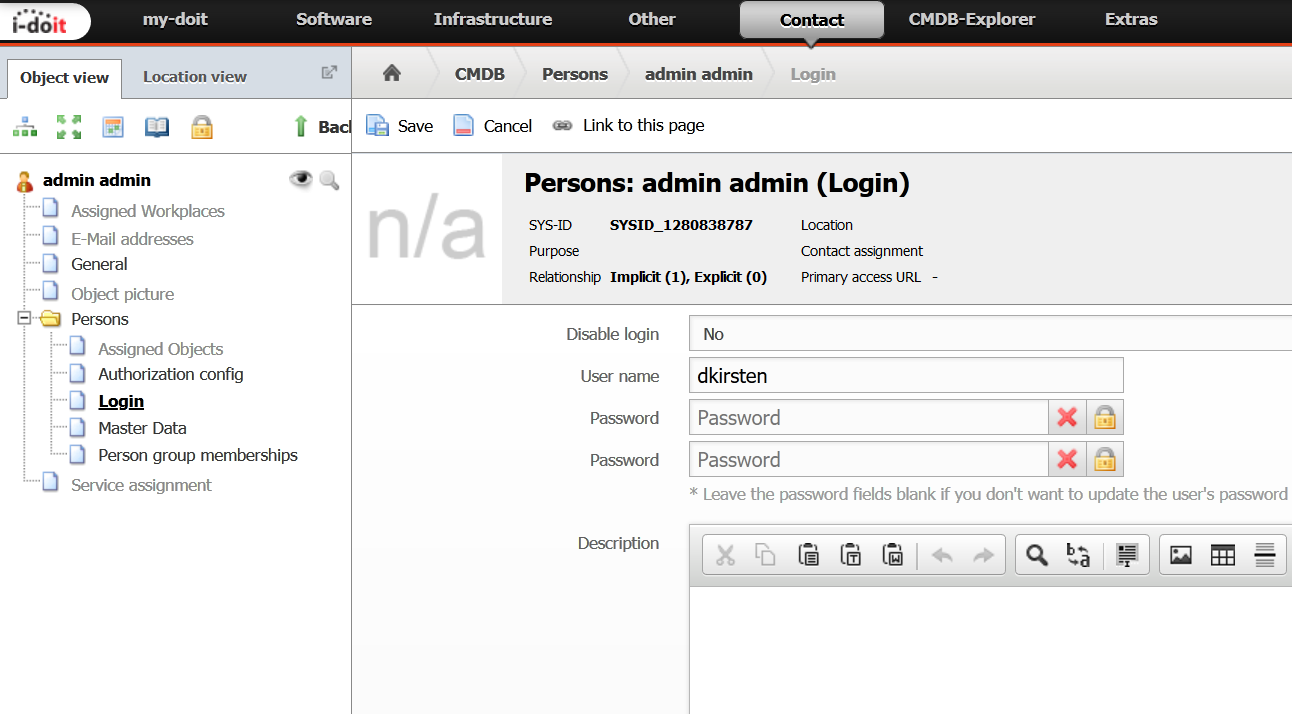
- Login into your i-doit and use this as the login name for the corresponding i-doit user
Warning
The domain part of the address, beginning with @ is not used. The name has to be reduced to the first part:“testaccount@i-doit.com” becomes “testaccount”.
Enable SSO in i-doit#
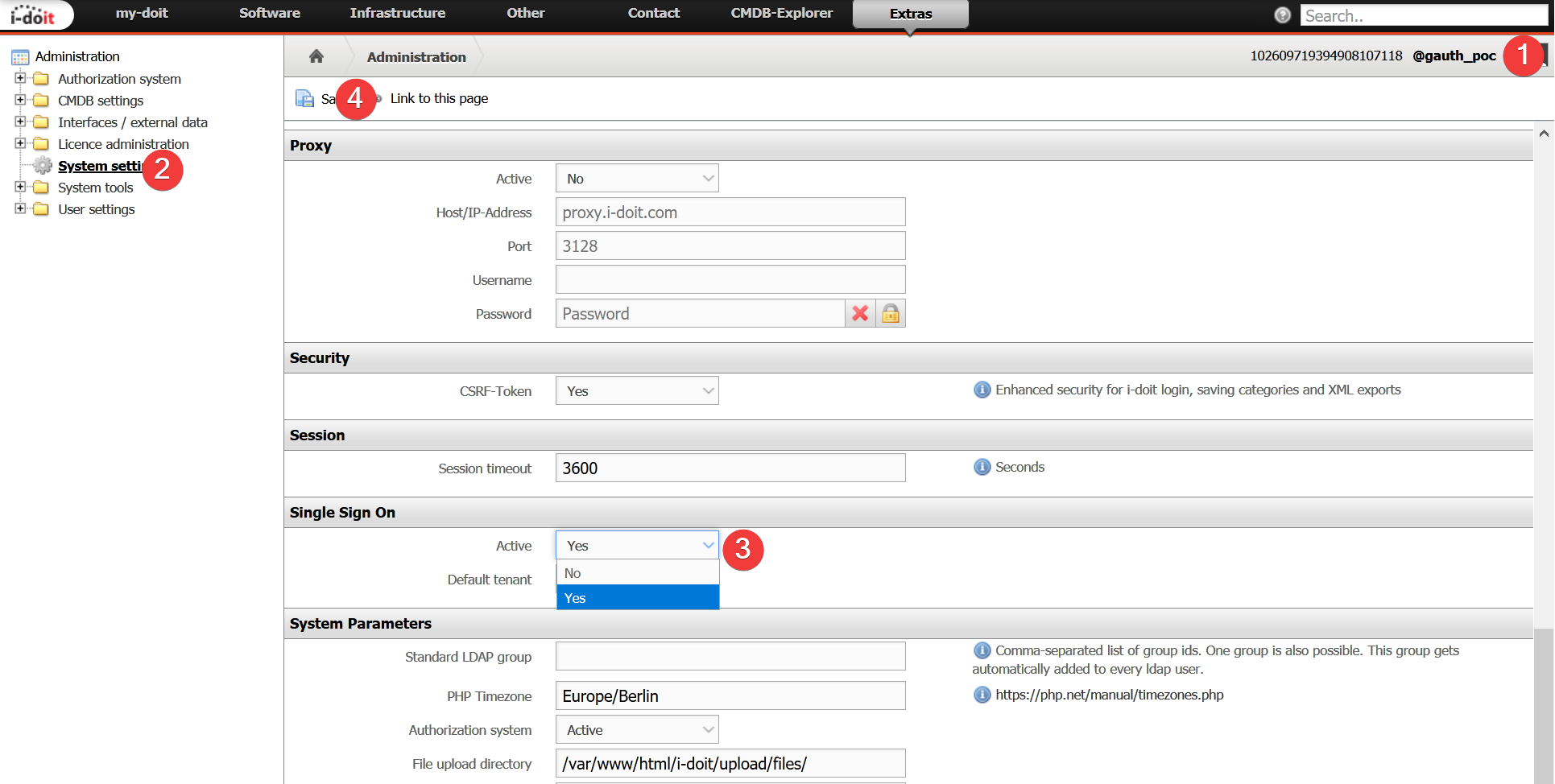
- Open your i-doit administration
- Select system settings
- Select "yes" at "Single Sign on" option "Active"
- Save
Done! If i-doit is now opened, the Google authentication appears first. After successful authentication, the user is directly logged in with the account linked to the user name.