ADFS (Active Directory) (SAML and Mellon)#
In this tutorial, we describe how to set up single sign-on (SSO) for i-doit using SAML. In this example, we use Mellon as an authenticator against LDAP-AD-FS.
Preparations#
We use two servers for the sample configuration, a Windows server with domain/AD and FS and a Debian 11 server with Apache and Mellon:
| FQDN | IP | Rolle | OS |
|---|---|---|---|
| tu2-dc2.tu-synetics.test | 10.10.60.22 | AD, FS | Windows |
| tu2-samlsso.synetics.test | 10.10.60.108 | Apache+Mellon | Debian11 |
Basic configuration#
✔ The Windows server must have a configured AD that includes the AD-FS role.
✔ I-doit is already pre-installed and usable.
Install packages#
1 | |
The system architecture should be x86 in 64bit.
Mellon Configuration#
We are creating a directory for this under /etc/apache2 and store our configuration data here.
1 2 | |
With the following command we create our Mellon metadata "Please adjust URLs"
1 | |
This now creates the following files
https\_tu2\_samlsso.synetics.test\_.cert
https\_tu2\_samlsso.synetics.test\_.key
https\_tu2\_samlsso.synetics.test\_.xml
Now we need to fetch the AD-FS metadata from our AD "Please adjust URLs"
1 | |
Now we need to create our Mellon configuration.
1 | |
Insert the following configuration directives based on the example:
1 2 3 4 5 6 7 8 | |
Apache2 Configuration#
First we create a self signed certificate "name can be individual".
1 | |
Example:
1 2 3 4 5 6 7 | |
Create VHost:
1 | |
Example:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 | |
In this example only the directory protected via Mellon is protected under /var/www/html. So we can create another VHost config later to install e.g. i-doit.
Creating the directory:
1 | |
Create an example html to test the call later on:
1 | |
Example:
1 2 3 4 5 6 7 8 | |
Test configuration:
1 | |
Activate Mods and Configs:
1 2 3 4 | |
Synchronize time:
1 | |
At this point, we are done with the configuration of the Linux server for the time being and can now turn our attention to our AD.
Configuration AD-FS#
First download the file mellon_metadata.xml from the Linux server e.g. via WinSCP and save it.
Claims aware remains active and then on Start
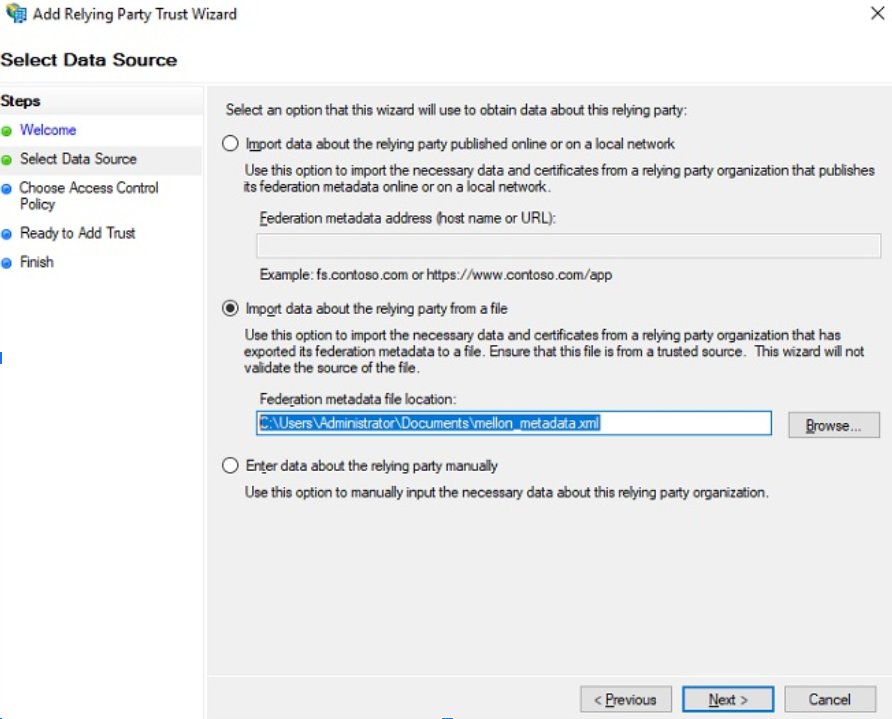
In the next step we select "import data ...." and navigate to our previously saved XML
The following note can be ignored if it appears.
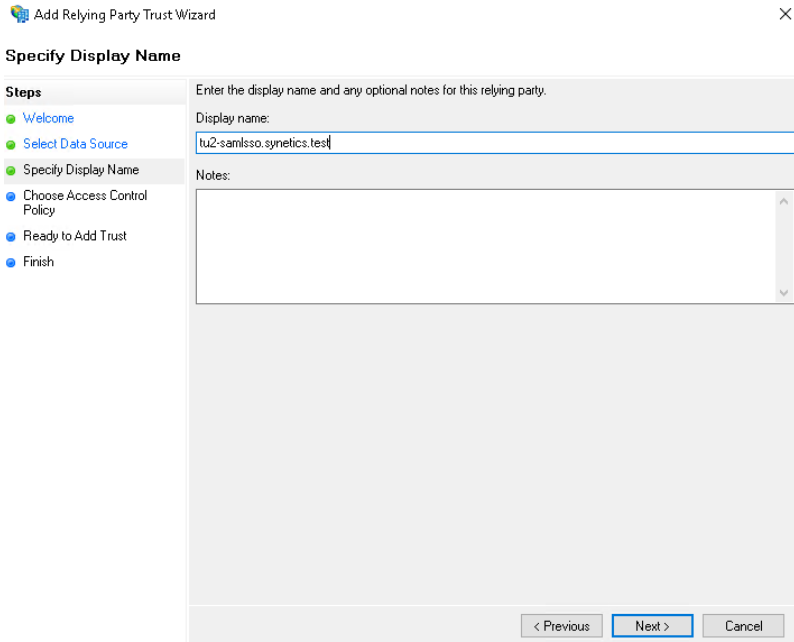
Now we enter the FQDN from our Linux server.
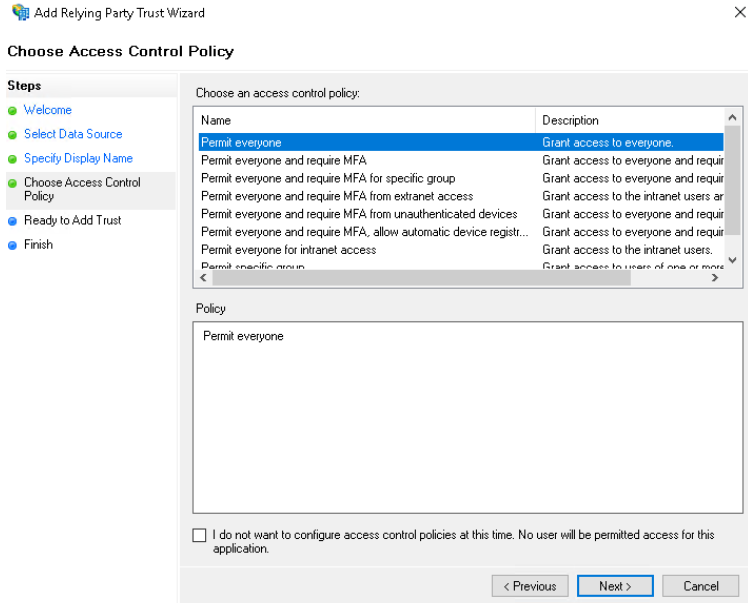
In the next step we can control accesses, for the sake of simplicity we leave it at Permit everyone for now.
We can also disregard the next window and just click next.
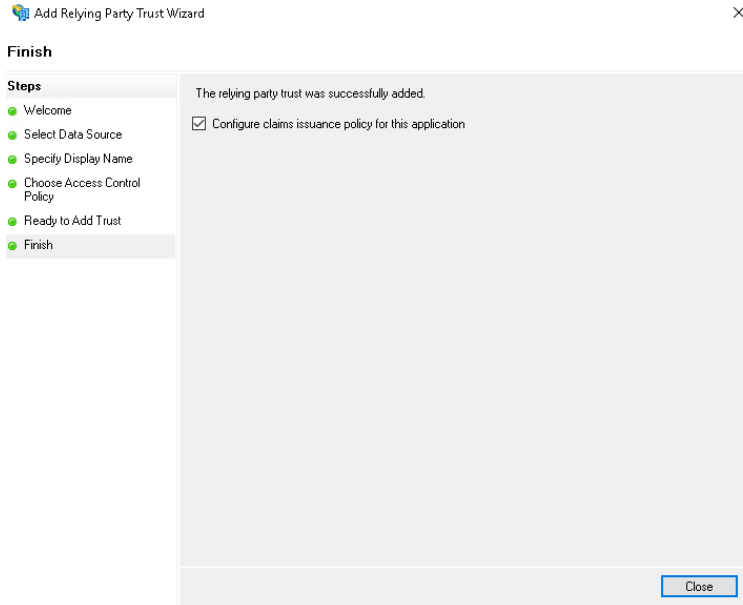
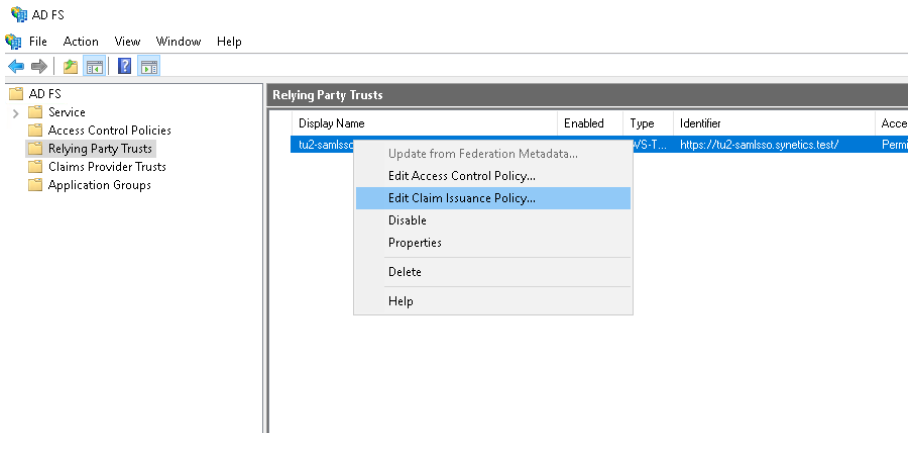
Finally only Close and the Party Trust is created
Now we need to define Claim Issuance Policies so that our user can also log in via mail.
Now a window opens and we click on Add Rule.
Now we select Send LDAP Attributes as Claim and click Next
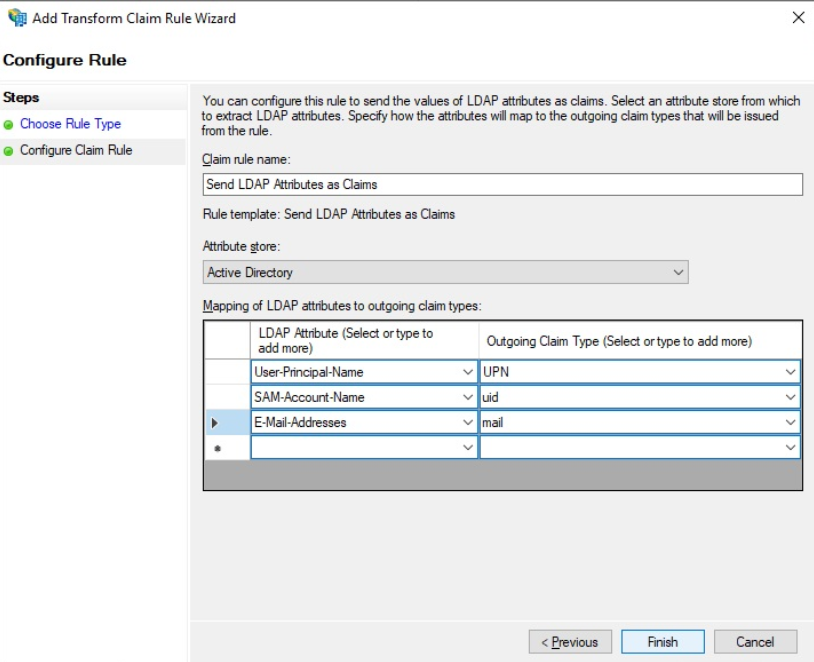
We give the rule a unique name and add the mapping as shown.
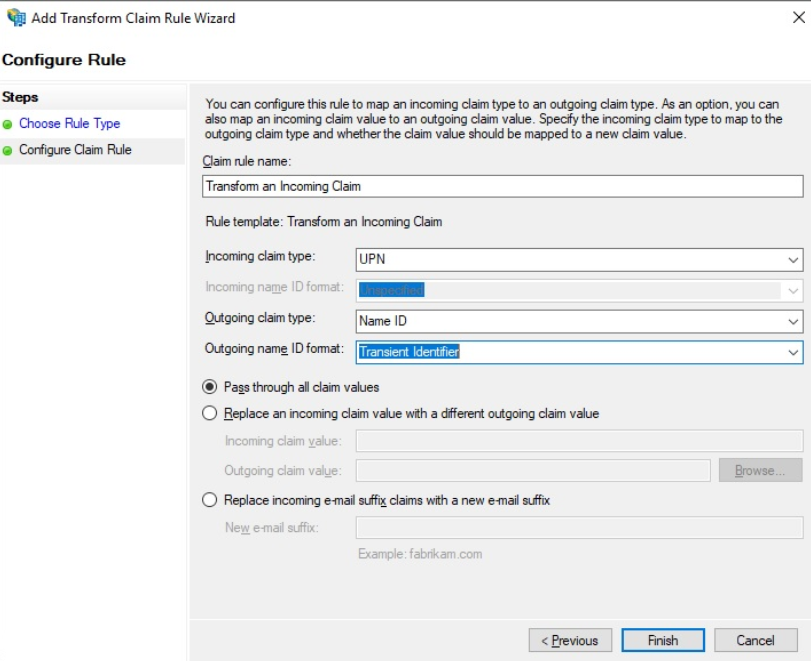
Then we create another rule and select Transform an Incoming Claim
Please configure as follows:
Now we have a fully configured Relying Party Trust and can test the authentication once.
Test SAML-SSO#
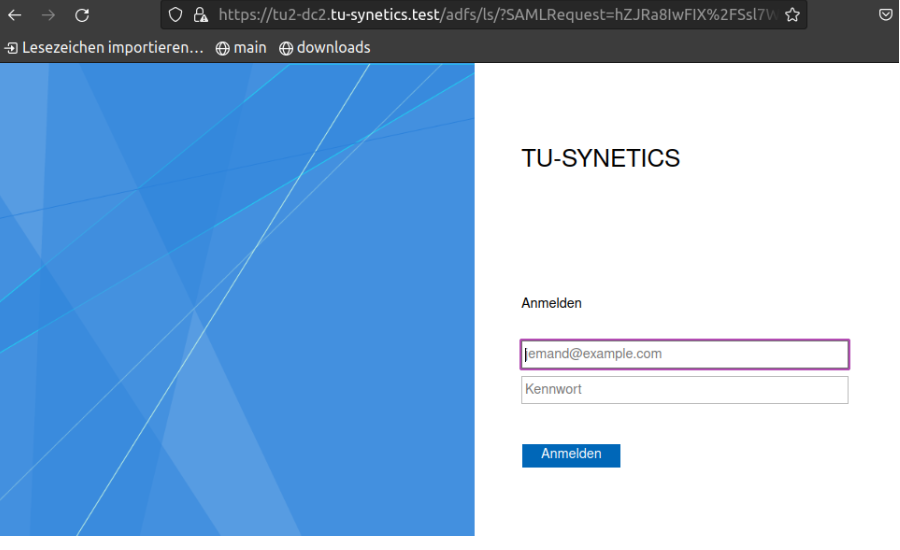
Open the URL from the server once in the browser Example: https://mywebserver.example.com/protected
After successful registration, we should receive the following output.
Installation i-doit#
The installation can be installed as described in the KB article for Debian.
SSO login for i-doit#
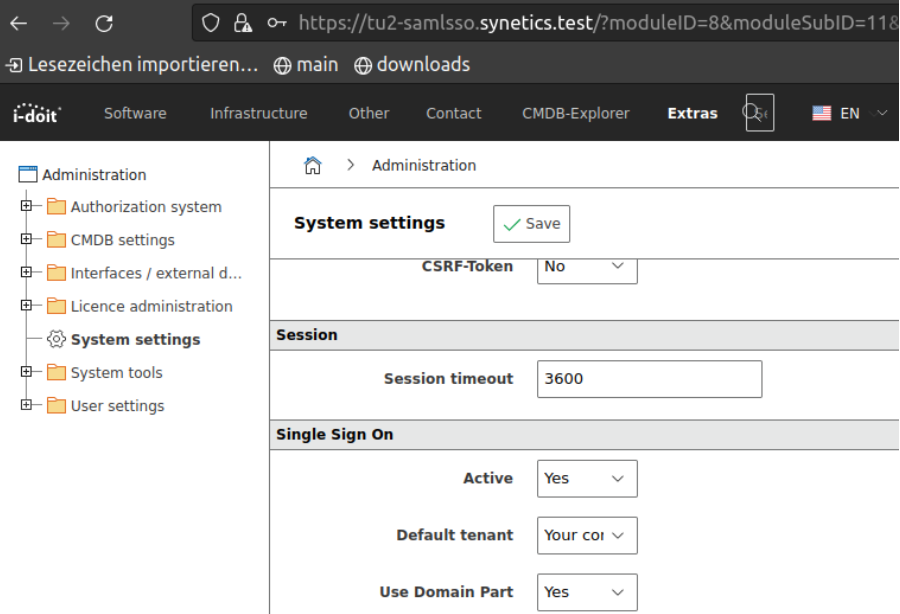
For this we have to go to System settings tab of the Admin-Center and adjust the configuration as follows.
Important information about contacts
It is mandatory that the e-mail address of the respective user is stored as login in i-doit!
Since we currently followed our instructions or KB, we need to adjust the VHost configuration so that we can now log in via SSO
Disable i-doit Vhost
1 | |
Customize Mellon Vhost created at the beginning
1 | |
Example:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 | |
Finally restart Apache once
1 | |
Finished!
If we now open the URL again in our browser and log in, we will be taken directly to the i-doit
Fallback to Logon Screen
If a user logs in who does not yet exist in i-doit, then this user is automatically redirected to the i-doit login screen and can log in with a local user.