Azure AD (SAML) authentication#
In this guide, we describe how to set up single sign-on (SSO) for i-doit using SAML. We will be using Mellon as an authenticator versus Azure AD via SAML ..
Preparations#
We use for the example configuration a Debian 11 server with Apache, Mellon and installed i-doit.
Basic configuration#
✔ This guide assumes that your Azure Active Directory has already been configured properly.
✔ i-doit is already pre-installed and usable.
Install packages#
1 | |
The system architecture should be x86 in 64bit.
Mellon configuration#
For this we create a directory under /etc/apache2 and put our configuration file here.
1 2 | |
With the following command we create our Mellon metadata "Customize URLs to your needs".
1 | |
The command will now create the following files:
1 2 3 | |
Now we have to create our Mellon configuration.
1 | |
The following directives are inserted based on the example:
1 2 3 4 5 6 7 8 | |
Apache2 configuration#
First we create a self signed certificate "name can be individual".
1 | |
Example:
1 2 3 4 5 6 7 | |
Create VHost:
1 | |
Example:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 | |
In this example, the directory /var/www/html/ where our i-doit is located is protected by using Mellon.
Activate i-doit SSO#
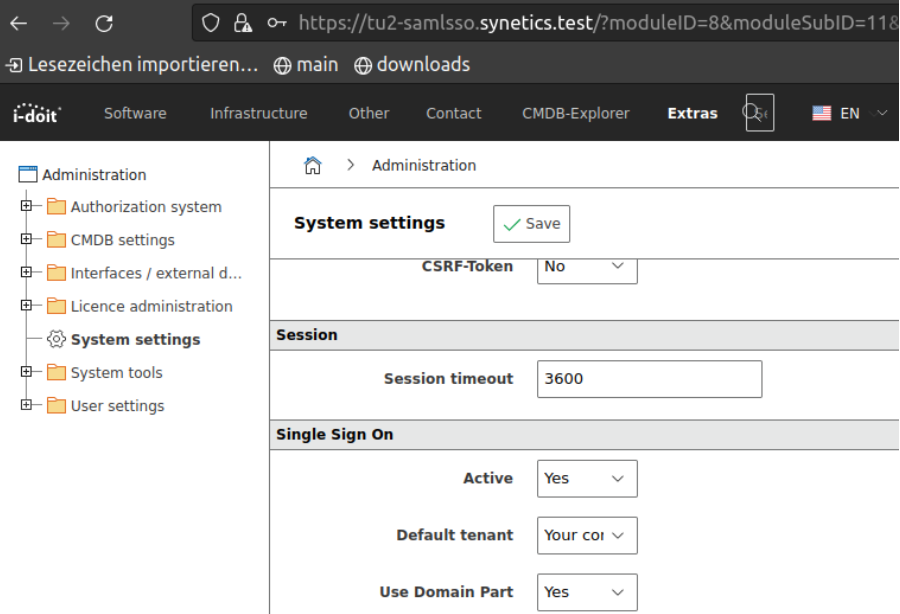
Now we have to go to the System settings tab of the Admin-Center and adjust the configuration as follows.
Important information about contacts
It is mandatory that the e-mail address of the respective user is stored as login in i-doit!
As long as the configurations on the Linux server have not been activated yet, users can still log in with the i-doit login mask and a local user.
Azure AD (SAML)#
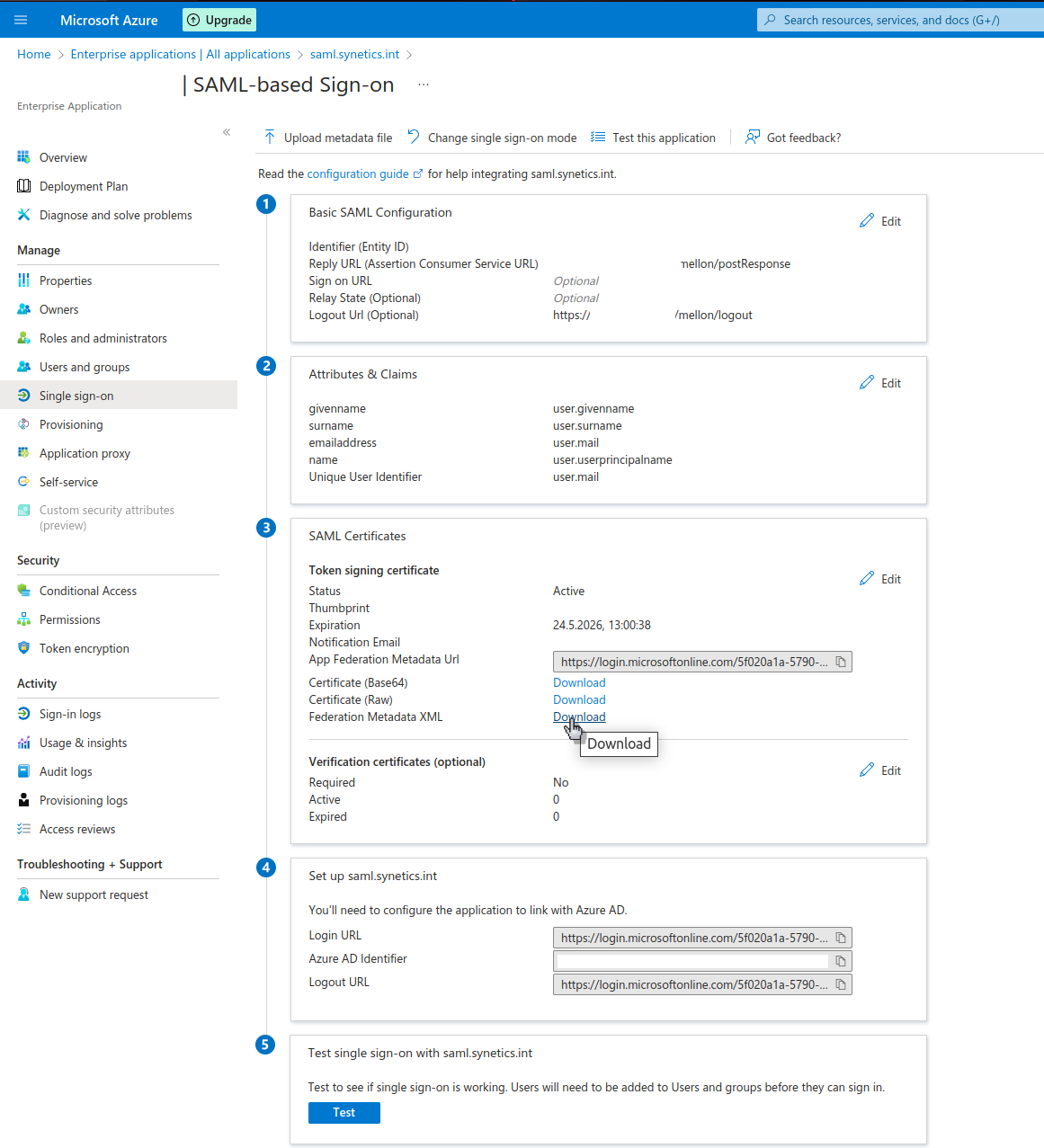
In order to get the required XML for the Mellon configuration we have to do the following steps (example):
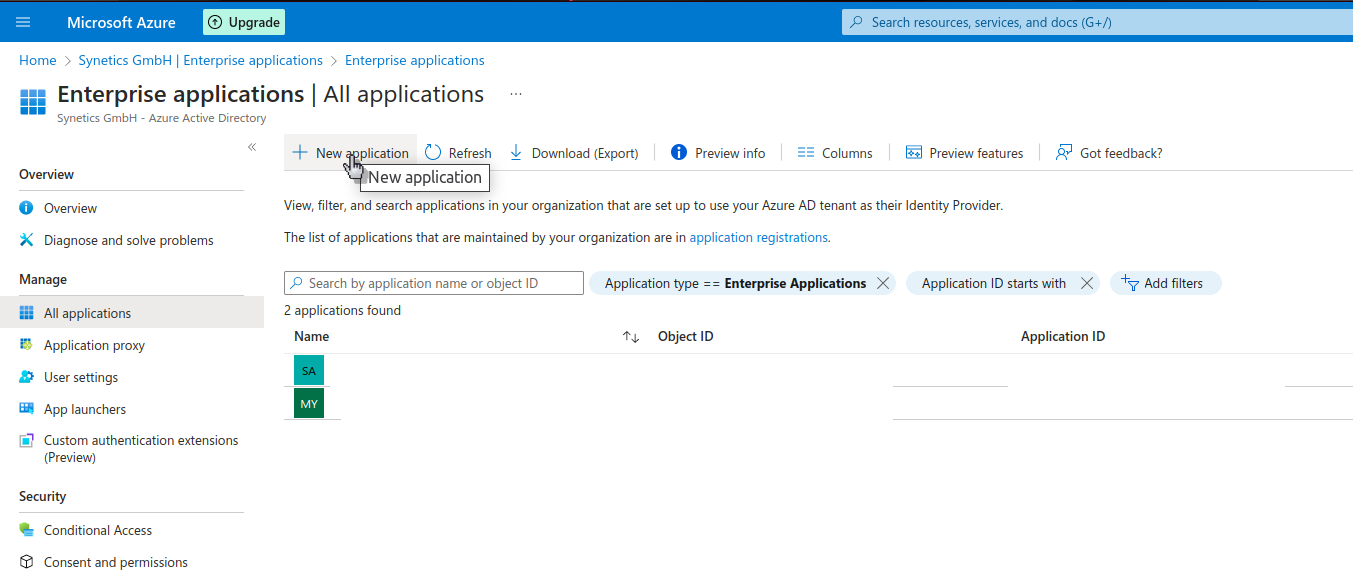
Create a enterprise application#
We log into Azure AD and then go to enterprise applications.
Create your own enterprise application.
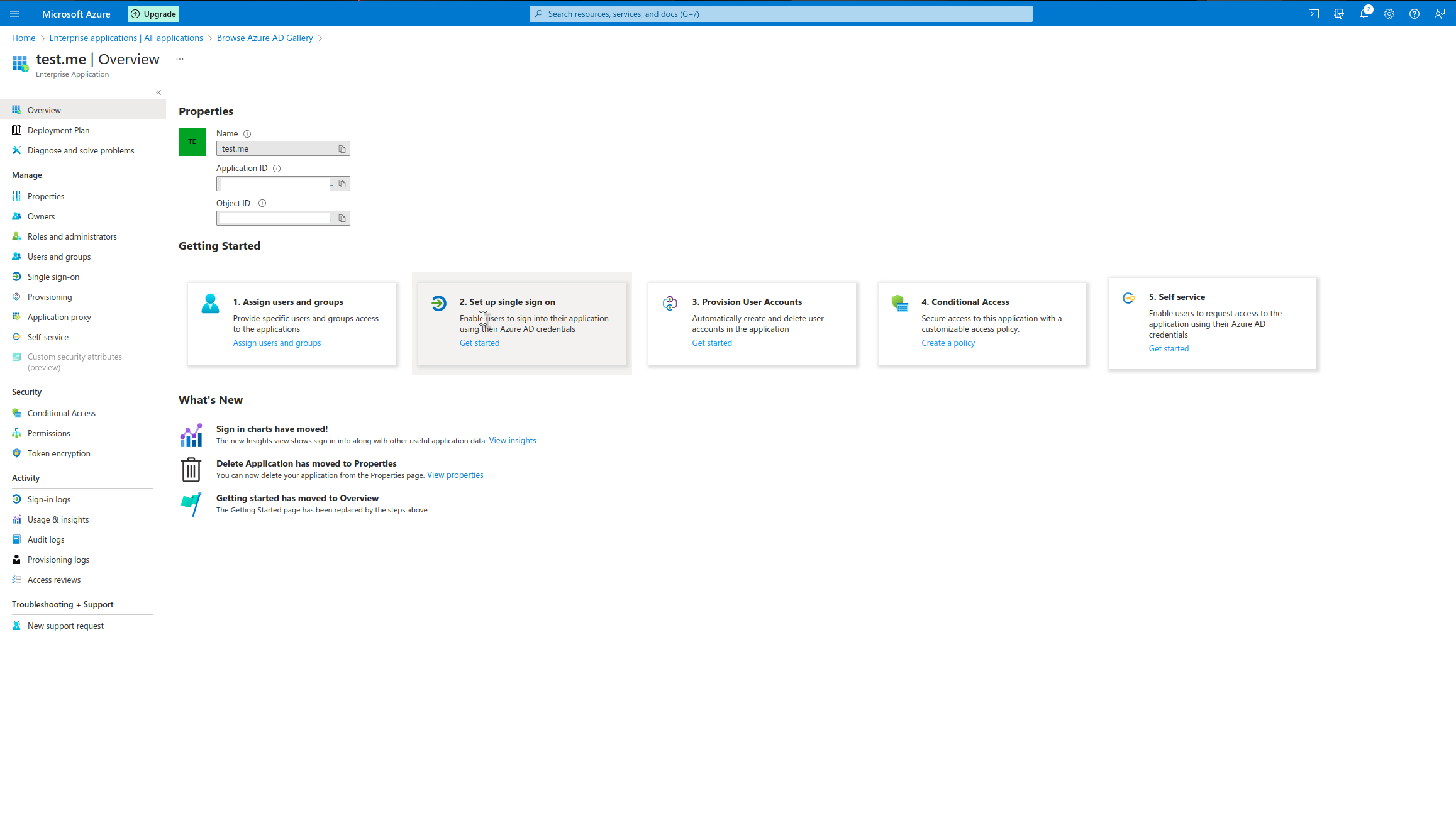
Set up SSO.
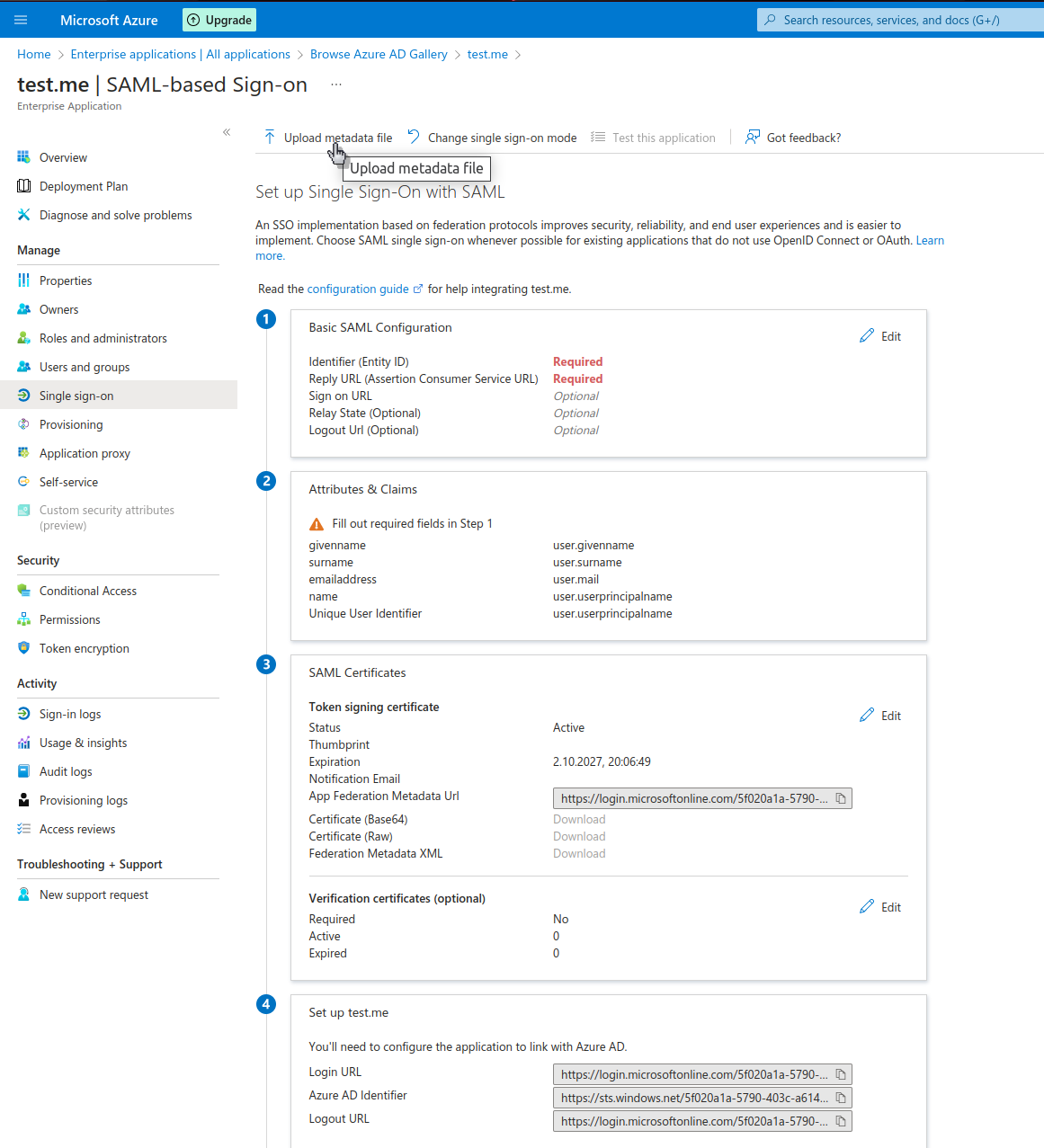
Now we select the SAML method and in the next step we provide our https_tu2_samlsso.synetics.test_.xml by clicking the button upload metadata file.
https_tu2_samlsso.synetics.test_.xml
The file must be downloaded beforehand from our server via e.g. SFTP.
Now we save the configuration.
Test
If a message appears asking to test the configuration, please confirm with the button No, I will test it later.
Afterwards we download the metadata XML because it will be needed later on.
In order for the users to gain access to the enterprise application, the assignment must be adjusted.
Lastly, we need to customize the unique user identifier so that Mellon can forward the user's email address to i-doit.
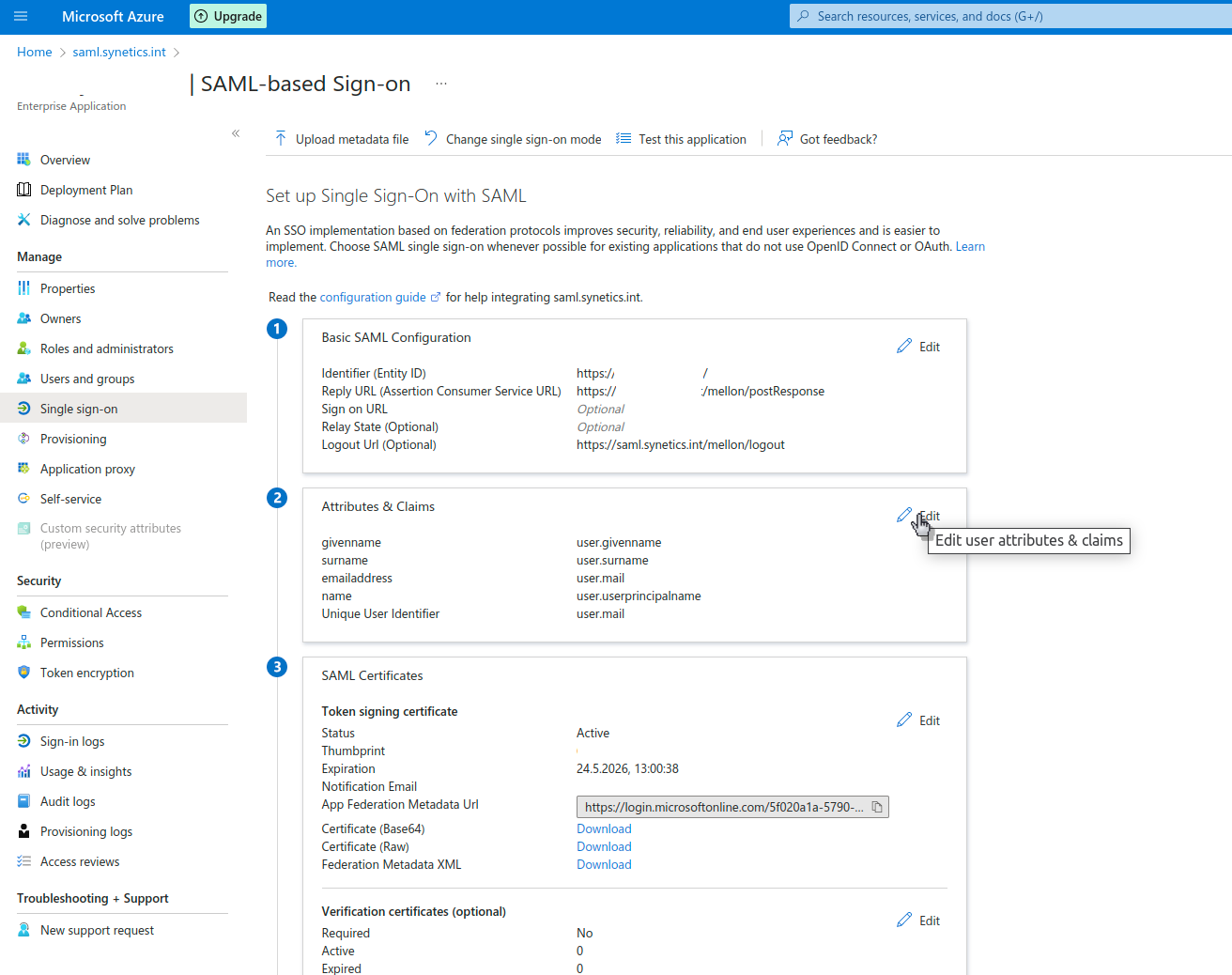
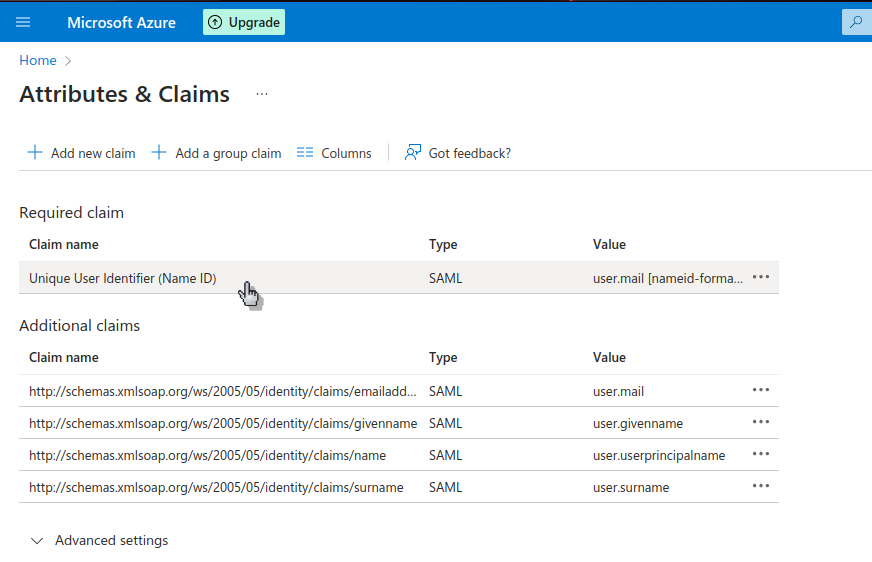
To do this, we open the Single sign-on item in the administration of the enterprise application. Then we see in the main area 'Attributes and claims' and we edit them.
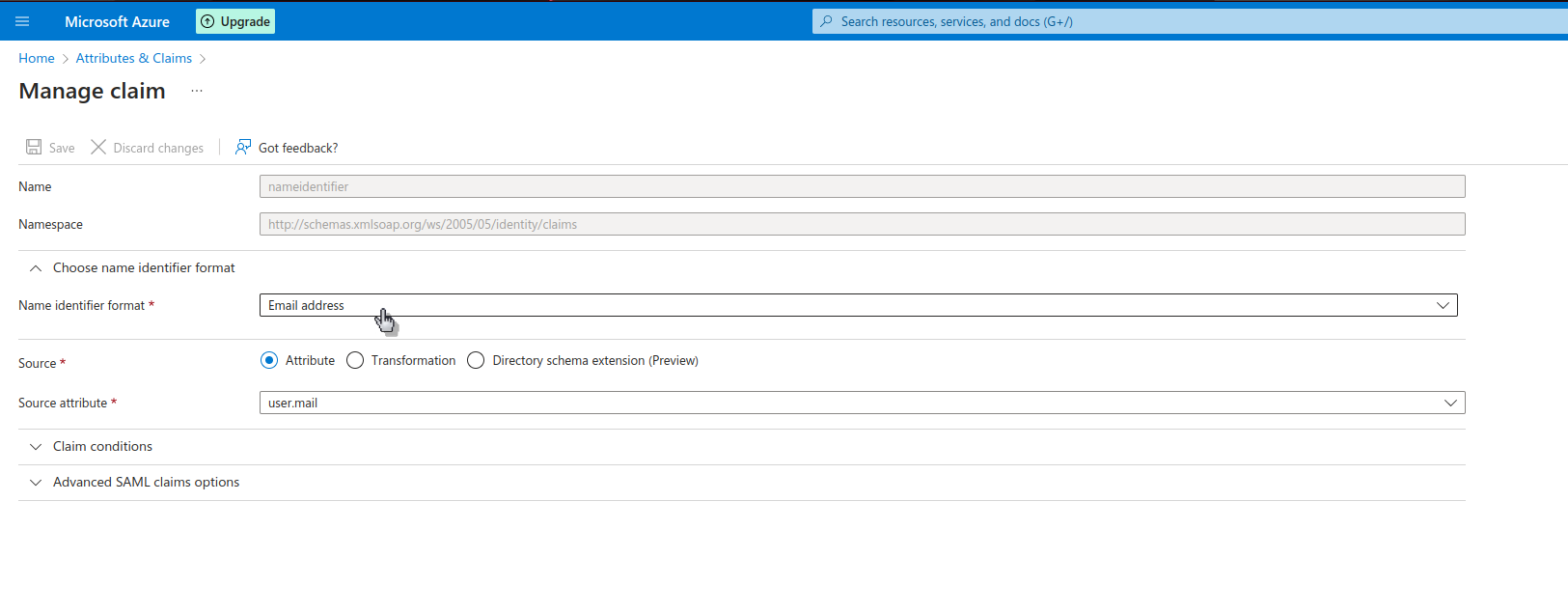
Now we edit under Successful claim the first claim that is displayed.
The name identifier format must be changed to email address mandatory. The source attribute must be changed to user.mail.. Then we save the configuration.
At this point, we are done configuring our enterprise application in Azure AD.
Activation of the configurations on the Linux server#
Provide metadata XML#
The previously created metadata XML must now be made available on our Linux server in the directory /etc/apache2/mellon so that Mellon can use it..
Filename
Please adjust the name of the file to AzureAD_metadata.xml in mellon.conf. Alternatively, adjust the filename in mellon.conf.
Now that we have created all the configurations so far, we can test them and activate all the necessary mods.
Test config#
1 | |
Activate mods and configs#
1 2 3 4 | |
At this point we are done with the configuration of our Linux server.
If we now open the URL again in our browser https://tu2-samlsso.synetics.test we will be redirected to the Azure AD login. After successful login we are redirected back to our i-doit and are successfully logged in.
Fallback to login screen
If a user logs in who does not yet exist in i-doit, then this user is automatically redirected to the i-doit login screen and can log in with a local user.